Good day!
Recently, copyright organizations and "K departments" in many countries have begun to pursue very aggressive policies against online anonymity and piracy. Particularly indicative are the stories from torrents.ru And ifolder.ru.
You can read more about Internet censorship in Wikipedia.
To protect the user and hoster from the “harmful” influence of the state and private companies, the I2P network was created. What is it and how to connect to I2P - read under the cut.

I2P is an anonymous encrypted network. It was introduced in 2003 by a community of developers advocating network security and anonymity.
By type of implementation it is overlay network and is located at layer 6 of the OSI model.
Each network client connects to other clients and forms tunnels through which traffic is transited (doesn’t it remind you of Skype?). The client program provides several interaction interfaces to other software:
The official I2P package includes:
All components are written in Java. If you haven’t changed your mind about installing it yet, then…
In the browser settings set the proxy server address: 127.0.0.1 port 4444.
The method is worse in that if you want to return to the regular Internet, you will have to return this setting.
Now you can open i2p sites, use anonymous torrents, mailers, etc..
Also, you can open the I2P router console and see what is there: http://127.0.0.1:7657
Several useful links:
forum.i2p — Official forum of the network. There is a Russian section.
ugha.i2p — English wiki about the network.
echelon.i2p — Repository of programs using I2P.
tracker2.postman.i2p —The largest BitTorrent network tracker.
rus.i2p — Russian-language wiki about I2P.
Other related articles:
I2P - Creating your own website
Recently, copyright organizations and "K departments" in many countries have begun to pursue very aggressive policies against online anonymity and piracy. Particularly indicative are the stories from torrents.ru And ifolder.ru.
You can read more about Internet censorship in Wikipedia.
To protect the user and hoster from the “harmful” influence of the state and private companies, the I2P network was created. What is it and how to connect to I2P - read under the cut.

So, let me bring you up to date
I2P is an anonymous encrypted network. It was introduced in 2003 by a community of developers advocating network security and anonymity.
By type of implementation it is overlay network and is located at layer 6 of the OSI model.
Each network client connects to other clients and forms tunnels through which traffic is transited (doesn’t it remind you of Skype?). The client program provides several interaction interfaces to other software:
- SOCKS—proxy—is the most commonly used protocol. Allows you to use I2P in conjunction with almost any program that supports it.
- SAM (Simple Anonymous Messaging) is a kind of API. Implemented on top of TCP.
- BOB (Basic Open Bridge) is another API. In fact, a modernized version of SAM, but using separate channels for commands and data.
The official I2P package includes:
- SusiDNS - DNS client
- Susimail - email client
- I2Psnark - torrent client
- I2PTunnel is an I2P integrated program that allows various TCP/IP services to communicate over I2P using tunnels
All components are written in Java. If you haven’t changed your mind about installing it yet, then…
Let's connect!
- If you do not have the JRE installed, install: java.com/download
- First, download and install the client: mirror.i2p2.de/i2pinstall_0.7.14.exe. Linux/Mac users: don’t pay attention to the extension, run it like this:
java -jar i2pinstall_0.7.14.exe

- Launching the client:
a. Windows:
Start -> I2P -> Start I2P (no window).
b. Unix-like:
Go to the client installation folder. Run the command:./i2prouter start
- Set the proxy server in the browser settings:
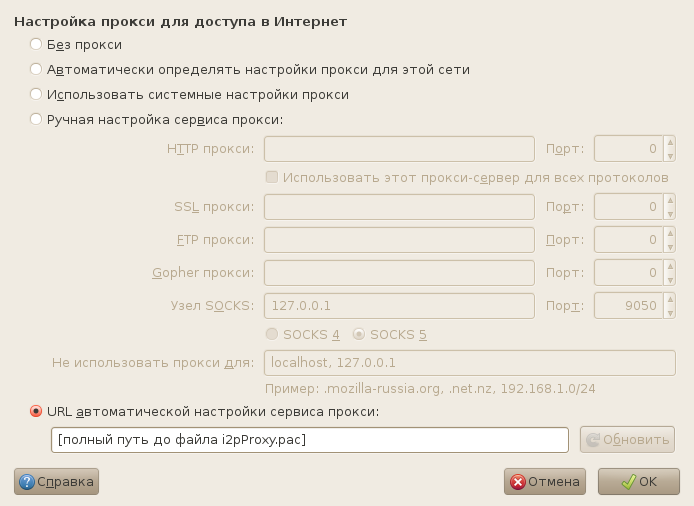
Method I: More difficult and better:
In the client installation folder in the scripts folder there is a file i2pProxy.pac.
In the browser settings, look for the line to enter the address of the auto-configuration of the proxy server:
Firefox:

Opera:

Method II: Simpler, but worse
In the browser settings set the proxy server address: 127.0.0.1 port 4444.
The method is worse in that if you want to return to the regular Internet, you will have to return this setting.
Ready!
Now you can open i2p sites, use anonymous torrents, mailers, etc..
Also, you can open the I2P router console and see what is there: http://127.0.0.1:7657
And finally...
Several useful links:
forum.i2p — Official forum of the network. There is a Russian section.
ugha.i2p — English wiki about the network.
echelon.i2p — Repository of programs using I2P.
tracker2.postman.i2p —The largest BitTorrent network tracker.
rus.i2p — Russian-language wiki about I2P.
Other related articles:
I2P - Creating your own website